 |
|
|
|
In the Forums... |
Posted: January 21, 2006 Last modified: January 26, 2006 Written By: Dan "Tweak Monkey" Kennedy Step 3 - Scan From Safe Mode Follow this process for best results from safe mode, closing programs as they finish: 1) Run CCleaner (Start, Programs, CCleaner). Click Run Cleaner. 2) Run Ad-Aware. Click Scan Now. The first option works OK. Click Next. The scan will take at least a few minutes so clean up your Start menu. Hover over any program you don't want a shortcut for and either Uninstall it or delete it (Right click, Delete). Click Next in Ad-Aware once it's finished then right click on the junk it found and choose Select All then Next, OK. 3) Run Spybot and click Check for Problems. After it's scanned choose Fix Selected Problems, Yes. 4) Run HiJackThis, choose Scan. Check all the items to remove that look bad based on the criteria from earlier (BHOs are OK to remove 100% of the time), choose Fix checked. 5) If the computer had any issues getting online, run the WinSock Fix and Reboot. 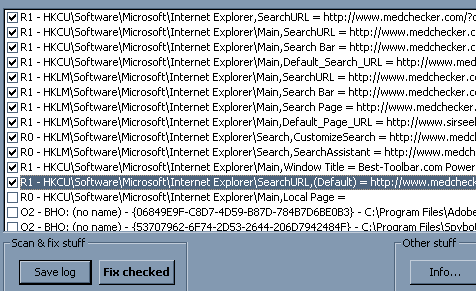 This program is the most effective of all of them. Step 4 - Scan From Regular Mode Run Microsoft Antispyware (Start, All Programs, Microsoft AntiSpyware) and perform a Full System Scan (you may need to select this in Scan Options). After it has removed everything tell it to restore your browser, Click Advanced Tools and Browser Restore. Now check Internet Explorer. If you have any more toolbars or pop-ups, repeat the process above. Otherwise read on to page 3. If you need to repeat the process, you may want to hit CTRL-ALT-DELETE and End Process (or right click and End Process Tree) on any programs you can including iexplore.exe and explorer.exe once the scans have started in Safe Mode. Pay extra attention when you run HiJackThis. Webroot Spy Sweeper is the best choice for removal and protection. There is not a free version of this software that allows you to remove spyware, but the free version can help find leftover traces (usually registry keys after the removal process). CCleaner can also clean up extra registry keys, temporary files, etc., using its extra tools. |
||
|
| |||
|---|---|---|---|